您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
這篇文章主要介紹“SpringBoot+Redis怎么實現防止惡意刷新與暴力請求接口”,在日常操作中,相信很多人在SpringBoot+Redis怎么實現防止惡意刷新與暴力請求接口問題上存在疑惑,小編查閱了各式資料,整理出簡單好用的操作方法,希望對大家解答”SpringBoot+Redis怎么實現防止惡意刷新與暴力請求接口”的疑惑有所幫助!接下來,請跟著小編一起來學習吧!
本項目采用 springboot+Redis的方式來實現;所采用的全部參考文獻在文末,包括軟件的安裝、測試等等
實驗環境: centos 7 安裝Redis ,采用wget安裝,
IDE :IDEA
pom文件:
<?xml version="1.0" encoding="UTF-8"?> <project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd"> <modelVersion>4.0.0</modelVersion> <groupId>org.example</groupId> <artifactId>springbootRefusePost</artifactId> <version>1.0-SNAPSHOT</version> <dependencies> <dependency> <groupId>org.projectlombok</groupId> <artifactId>lombok</artifactId> <version>RELEASE</version> <scope>compile</scope> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-data-redis</artifactId> <version>2.3.0.RELEASE</version> </dependency> <dependency> <groupId>com.alibaba</groupId> <artifactId>fastjson</artifactId> <version>1.2.67</version> </dependency> <dependency> <groupId>com.fasterxml.jackson.core</groupId> <artifactId>jackson-annotations</artifactId> <version>2.13.1</version> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-test</artifactId> <version>2.3.3.RELEASE</version> </dependency> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> <version>2.3.3.RELEASE</version> </dependency> </dependencies> </project>
因為只測試了一個接口暴力請求,所以并沒有分包,對于全局異常只是在后臺拋出,并沒有在前端做全局的捕獲返回
飄紅的原因是idea的受檢異常,可忽略
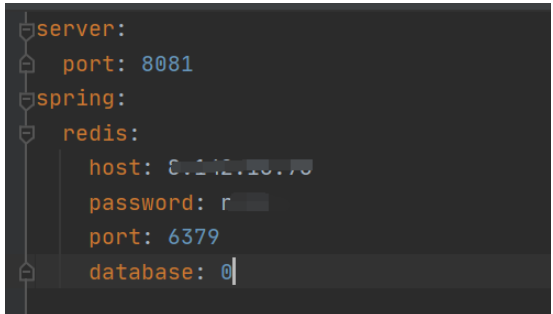
application.yml配置類
文章中用到的六個類包括啟動類如下所示:
package com.ApiTest;
import java.lang.annotation.ElementType;
import java.lang.annotation.Retention;
import java.lang.annotation.RetentionPolicy;
import java.lang.annotation.Target;
/**
* 自定義注解,用于攔截過于頻繁的請求
*/
@Retention(RetentionPolicy.RUNTIME)
@Target(ElementType.METHOD)
public @interface AccessLimit {
int seconds();
int maxCount();
boolean needLogin() default true;
}package com.ApiTest;
import com.ApiTest.MyException;
import com.ApiTest.AccessLimit;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.stereotype.Component;
import org.springframework.web.method.HandlerMethod;
import org.springframework.web.servlet.HandlerInterceptor;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.util.concurrent.TimeUnit;
/**
* 自定義攔截器
*/
@Component
public class AccessLimtInterceptor implements HandlerInterceptor {
@Autowired
private RedisTemplate redisTemplate;
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws Exception {
if (handler instanceof HandlerMethod) {
HandlerMethod hm = (HandlerMethod) handler;
AccessLimit accessLimit = hm.getMethodAnnotation(AccessLimit.class);
if (null == accessLimit) {
return true;
}
int seconds = accessLimit.seconds();
int maxCount = accessLimit.maxCount();
boolean needLogin = accessLimit.needLogin();
if (needLogin) {
//判斷是否登錄
}
String ip=request.getRemoteAddr();
String key = request.getServletPath() + ":" + ip ;
System.out.println(ip);
System.out.println(key);
//獲取key鍵對應的值。
Integer count = (Integer) redisTemplate.opsForValue().get(key);
System.out.println(count);
if (null == count || -1 == count) {
//redisTemplate.opsForValue().set 增?個字符串類型的值,key是鍵,value是值。
//?法含義:新增?個字符串類型的值,并且設置變量值的過期時間。key是鍵,value是值,timeout 過期時間,unit 過期時間單位
//鏈接:https://wenku.baidu.com/view/f0de3ecc1ae8b8f67c1cfad6195f312b3169ebd1.html
System.out.println("初次進入");
redisTemplate.opsForValue().set(key, 1,seconds, TimeUnit.SECONDS);
return true;
}
if (count < maxCount) {
count = count+1;
//?法含義:覆蓋從指定位置開始的值
redisTemplate.opsForValue().set(key, count,0);
return true;
}
// response 返回 json 請求過于頻繁請稍后再試
throw new MyException("20001","操作過于頻繁");
}
return true;
}
}package com.ApiTest;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.ResponseBody;
import org.springframework.web.bind.annotation.RestController;
@RestController
public class AppHomeController {
@GetMapping("/index")
@AccessLimit(seconds = 2, maxCount = 5) //2秒內 允許請求5次
@ResponseBody
public String getImageList(){
return "請求成功";
}
}package com.ApiTest;
/**
* 自定義異常類
*/
public class MyException extends Exception {
// 異常代碼
private String code;
//異常信息
private String message;
//構造方法
public MyException(String code, String message) {
this.code = code;
this.message = message;
}
public String getCode() {
return code;
}
public void setCode(String code) {
this.code = code;
}
@Override
public String getMessage() {
return message;
}
public void setMessage(String message) {
this.message = message;
}
}package com.ApiTest;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.servlet.config.annotation.InterceptorRegistry;
import org.springframework.web.servlet.config.annotation.WebMvcConfigurerAdapter;
/**
* 在webconfig中配置攔截器
*/
@Configuration
public class MyWebMvcConfigurer extends WebMvcConfigurerAdapter {
@Autowired
private AccessLimtInterceptor accessLimtInterceptor;
@Override
public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(accessLimtInterceptor);
super.addInterceptors(registry);
}
}
```java
package com;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.context.annotation.Bean;
import org.springframework.web.client.RestTemplate;
@SpringBootApplication
public class Application {
@Bean
public RestTemplate restTemplate() {
return new RestTemplate();
}
public static void main(String[] args) {
SpringApplication.run(Application.class, args);
}
}到此,關于“SpringBoot+Redis怎么實現防止惡意刷新與暴力請求接口”的學習就結束了,希望能夠解決大家的疑惑。理論與實踐的搭配能更好的幫助大家學習,快去試試吧!若想繼續學習更多相關知識,請繼續關注億速云網站,小編會繼續努力為大家帶來更多實用的文章!
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。