您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
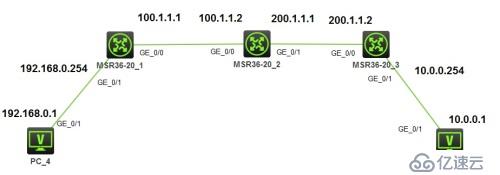
一:目的:100.1.1.1與200.1.1.2建立ipsec隧道。
二:配置基本命令
1 配置acl :
[MSR_1]acl advanced 3000
[MSR_1-acl-ipv4-adv-3000]rule permit ip source 192.168.0.1 0 destination 10.0.0.1 0
2創建IPsec安全提議
[MSR_1]ipsec transform-set tran
[MSR_1-ipsec-transform-set-tran]encapsulation-mode tunnel
[MSR_1-ipsec-transform-set-tran]protocol esp
[MSR_1-ipsec-transform-set-tran]esp encryption-algorithm aes-cbc-128
[MSR_1-ipsec-transform-set-tran]esp authentication-algorithm sha1
3創建IKE keychain
[MSR_1]ike keychain test
[MSR_1-ike-keychain-test]pre-shared-key address 200.1.1.2 255.255.255.0 key simple 123456
4創建IKE提議
[MSR_1]ike proposal 100
[MSR_1-ike-proposal-100]encryption-algorithm 3des-cbc
[MSR_1-ike-proposal-100]authentication-method pre-share
[MSR_1-ike-proposal-100]authentication-algorithm md5
[MSR_1-ike-proposal-100]dh group1
5創建IKE profile
[MSR_1]ike profile profile1
[MSR_1-ike-profile-profile1]keychain test
[MSR_1-ike-profile-profile1]local-identity address 100.1.1.1
[MSR_1-ike-profile-profile1]match remote identity address 200.1.1.2 255.255.255.0
[MSR_1-ike-profile-profile1]proposal 100
6創建一條IKE協商方式的IPsec安全策略
[MSR_1]ipsec policy test 10 isakmp
[MSR_1-ipsec-policy-isakmp-test-10]remote-address 200.1.1.2
[MSR_1-ipsec-policy-isakmp-test-10]security acl 3000
[MSR_1-ipsec-policy-isakmp-test-10]transform-set tran
[MSR_1-ipsec-policy-isakmp-test-10]ike-profile profile1
7接口應用:
[MSR_1]int g0/0
[MSR_1-GigabitEthernet0/0]ipsec apply policy test
另端設備鏡像配置即可。
三:抓包:
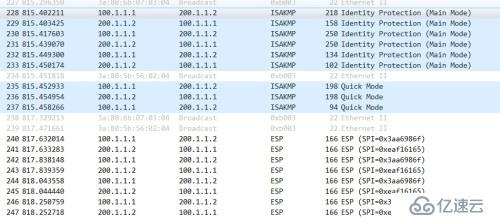
esp數據包: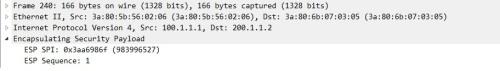
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。