您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
-----對于路由器通過tunnel接口建立不需知道感興趣流的L2L ×××,配置反向路由注入覺得應該是沒有作業的
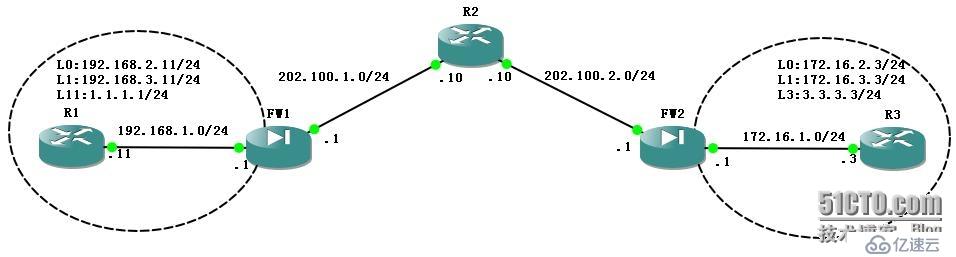
----參照以前的博文:http://333234.blog.51cto.com/323234/1253465
A.基本配置:
①FW1:
----接口配置:
interface Ethernet0
nameif Inside
security-level 100
ip address 192.168.1.1 255.255.255.0
no shut
interface Ethernet1
nameif Outside
security-level 0
ip address 202.100.1.1 255.255.255.0
no shut
----路由配置:
route Outside 0.0.0.0 0.0.0.0 202.100.1.10
----策略配置:
access-list OUTSIDE extended permit icmp any any
access-group OUTSIDE in interface Outside
----PAT配置:
access-list PAT extended permit ip 192.168.0.0 255.255.0.0 any
access-list NONAT extended permit ip 192.168.0.0 255.255.0.0 172.16.0.0 255.255.0.0
global (Outside) 1 interface
nat (Inside) 0 access-list NONAT
nat (Inside) 1 access-list PAT
②FW2:
----接口配置:
interface Ethernet0
nameif Inside
security-level 100
ip address 172.16.1.1 255.255.255.0
no shut
interface Ethernet1
nameif Outside
security-level 0
ip address 202.100.2.1 255.255.255.0
no shut
----路由配置:
route Outside 0.0.0.0 0.0.0.0 202.100.2.10
----策略配置:
access-list OUTSIDE extended permit icmp any any
access-group OUTSIDE in interface Outside
----PAT配置:
access-list PAT extended permit ip 172.16.0.0 255.255.0.0 any
access-list NONAT extended permit ip 172.16.0.0 255.255.0.0 192.168.0.0 255.255.0.0
global (Outside) 1 interface
nat (Inside) 0 access-list NONAT
nat (Inside) 1 access-list PAT
B.×××配置:
①FW1:
----第一階段策略:
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
tunnel-group 202.100.2.1 type ipsec-l2l
tunnel-group 202.100.2.1 ipsec-attributes
pre-shared-key cisco
----第二階段轉換集:
crypto ipsec transform-set transet esp-des esp-md5-hmac
----感興趣流:
access-list ××× extended permit ip 192.168.0.0 255.255.0.0 172.16.0.0 255.255.0.0
④配置crypto map并應用、在接口開啟isakmp:
crypto map crymap 20 match address ×××
crypto map crymap 20 set peer 202.100.2.1
crypto map crymap 20 set transform-set transet
crypto map crymap interface Outside
crypto isakmp enable Outside
①FW2:
----第一階段策略:
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
tunnel-group 202.100.1.1 type ipsec-l2l
tunnel-group 202.100.1.1 ipsec-attributes
pre-shared-key cisco
----第二階段轉換集:
crypto ipsec transform-set transet esp-des esp-md5-hmac
----感興趣流:
access-list ××× extended permit ip 172.16.0.0 255.255.0.0 192.168.0.0 255.255.0.0
④配置crypto map并應用、在接口開啟isakmp:
crypto map crymap 20 match address ×××
crypto map crymap 20 set peer 202.100.1.1
crypto map crymap 20 set transform-set transet
crypto map crymap interface Outside
crypto isakmp enable Outside
C.測試:
①不用觸發×××,查看防火墻的outside接口路由,可以看到只有一條默認路由
----因為沒有配置反向路由注入
FW1(config)# show route outside
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 202.100.1.10 to network 0.0.0.0
C 202.100.1.0 255.255.255.0 is directly connected, Outside
S* 0.0.0.0 0.0.0.0 [1/0] via 202.100.1.10, Outside
FW1(config)#
②增加反向路由注入配置,也不用觸發×××,可以看到outside多一條靜態路由
FW1(config)# crypto map crymap 20 set reverse-route
FW1(config)# show route outside
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 202.100.1.10 to network 0.0.0.0
S 172.16.0.0 255.255.0.0 [1/0] via 202.100.1.10, Outside
C 202.100.1.0 255.255.255.0 is directly connected, Outside
S* 0.0.0.0 0.0.0.0 [1/0] via 202.100.1.10, Outside
③修改感興趣流的ACL,靜態路由也跟著變化
FW1(config)# access-list ××× extended permit ip 192.168.1.0 255.255.255.0 172.16.1.0 255.255.255.0
FW1(config)# show route outside
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 202.100.1.10 to network 0.0.0.0
S 172.16.0.0 255.255.0.0 [1/0] via 202.100.1.10, Outside
S 172.16.1.0 255.255.255.0 [1/0] via 202.100.1.10, Outside
C 202.100.1.0 255.255.255.0 is directly connected, Outside
S* 0.0.0.0 0.0.0.0 [1/0] via 202.100.1.10, Outside
----原有的感興趣流沒有刪除,只是增加了一條更詳細的ACL,靜態路由也增加了一條更詳細的路由
----由此可見,反向路由注入的條目只是的感興趣流的目標網絡有關,并且與是否觸發×××也沒有關系
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。