您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
前言
在介紹和使用tcpdump之前,請確保您已經掌握或者了解如下幾個關鍵概念,否則后面的內容讓你有點痛苦。
能夠在Linux命令行下工作
理解OSI七層網絡協議的概念
熟悉各層的協議頭部,重點是IP/TCP/UDP
交換機和路由器對應于OSI的協議層
另外還需要注意的是:
tcpdump是基于Unix系統的命令行式的數據包嗅探工具。如果要使用tcpdump抓取其他主機MAC地址的數據包,必須開啟網卡混雜模式,所謂混雜模式,用最簡單的語言就是讓網卡抓取任何經過它的數據包,不管這個數據包是不是發給它或者是它發出的,點擊【http://en.wikipedia.org/wiki/Promiscuous_mode】獲取更多有關混雜模式的資料。一般而言,Unix不會讓普通用戶設置混雜模式,因為這樣可以看到別人的信息,比如telnet的用戶名和密碼,這樣會引起一些安全上的問題,所以只有root用戶可以開啟混雜模式,開啟混雜模式的命令是:ifconfig eth0 promisc, eth0是你要打開混雜模式的網卡。肯定有人要問如果在windows下要不要打開混雜模式,windows下網卡沒有什么混雜模式不混雜模式,在于應用程序本身,如使用Wireshark抓包的時候可以通過設置為在混雜模式下抓包(這就是為什么該死的ARP欺騙病毒可以猖狂的原因)。tcpdump當然也可以指定抓包過濾器,而且其過濾器語言非常著名,叫做Berkeley包過濾,簡稱BPF語言。
tcpdump介紹
tcpdump is the premier network analysis tool for information security professionals. tcpdump is a commandline network analyzer tool or more technically a packet sniffer. Having a solid grasp of this uber-powerful application is mandatory for anyone desiring a thorough understanding of TCP/IP. It can be thought of as the commandline version of wiresharek (only to a certain extent, since wireshark is much more powerful and capable. Many prefer to use higher level analysis tools Wireshark, but I believe this to usually be a mistake, you must know how wireshark work).
As a commandline tool tcpdump is quite powerful for network analysis as filter expressions can be passwd in and tcpdump would pick up only the matching packets and dump them.
安裝tcpdump
### CentOS [root@localhost ~]# yum search tcpdump ======================== Matched: tcpdump =============================== arpwatch.i386 : Network monitoring tools for tracking IP addresses on a network. libpcap.i386 : A system-independent interface for user-level packet capture. libpcap-devel.i386 : A pcap library. tcpdump.i386 : A network traffic monitoring tool. [root@localhost ~]# yum -y install tcpdump ### Ubuntu $ sudo apt-get install tcpdump
對于Linux,tcpdump 依賴于libpcap庫,關于更多libpcap庫,請參考這里。
tcpdump命令行選項
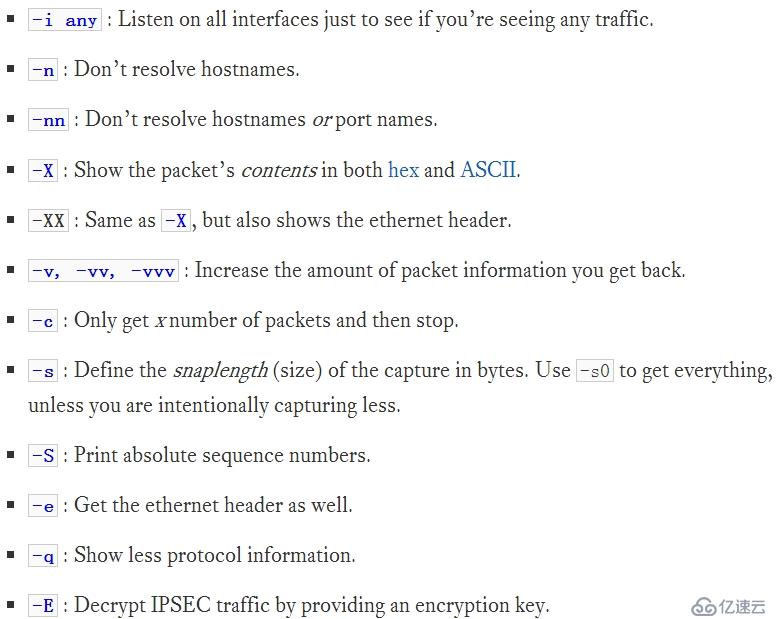
下面的一些選項能夠幫助我們更好的利用tcpdump工作。這些選項非常容易忘記而且比較容易混淆,所以,請時刻 man 一下。

首先,我會根據實際情況,喜歡添加一些選項在tcpdump命令本身。第一個是 -n ,不進行名稱解析,結果以IP地址的形式展現。第二個是 -X, 它以十六進制和ASCII把包的內容顯示。最后一個是 -S,以絕對序列號顯示,而不是相對的。
需要重點關注的是,默認情況下,tcpdump只會抓取包的前96 bytes,如果你想抓取更多,請加上 -s number 選項,number 指定您想抓取的字節數。我建議使用 0(zero) 作為抓取的字節number,這將抓取所有的數據包的所有內容。
下面是我經常使用的選項:
tcpdump基本用法
1、-n Don't convert host addresses to names. This can be used to avoid DNS
lookups.
[root@localhost ~]# tcpdump -n tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes 17:25:33.472001 IP 192.168.27.129.46255 > 192.168.27.2.53: 36340+ A? www.baidu.com. (31)
默認情況下,tcpdump將監視第一個網卡上所有流過的數據包,我們看一下tcpdump輸出的這一行信息。
第一個字段"17:25:33.472001",是毫秒級精度的時間戳。
第二個字段"IP",是數據包的協議。
第三個字段"192.168.27.129.46255",是source IP Address joined with the source Port。
第四個字段"192.168.27.2.53",是destination IP Address joined with destination Port and then some information about the packet.
2、-v -vv -vvv verbose, very verbose, very very verbose
-S Print absolute, rather than relative, TCP sequence numbers.
[root@localhost ~]# tcpdump -nnvvS
3、-X Print each packet (minus its link level header) in hex and ASCII.
[root@localhost ~]# tcpdump -nnvvXS
4、-s increases the default snaplength, grabbing the whole packet
[root@localhost ~]# tcpdump -nnvvXS -s 1514 [root@localhost ~]# tcpdump -nnvvXS -s0
5、capture of exactly two(-c2) ICMP packets(a ping)
[root@localhost ~]# tcpdump -nnvvXS -s0 -c2 tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 19:20:16.361251 IP (tos 0x0, ttl 64, id 28517, offset 0, flags [DF], proto: UDP (17), length: 59) 192.168.27.129.56183 > 192.168.27.2.53: [udp sum ok] 8002+ A? www.baidu.com. (31) 0x0000: 4500 003b 6f65 4000 4011 1379 c0a8 1b81 E..;oe@.@..y.... 0x0010: c0a8 1b02 db77 0035 0027 90dc 1f42 0100 .....w.5.'...B.. 0x0020: 0001 0000 0000 0000 0377 7777 0562 6169 .........www.bai 0x0030: 6475 0363 6f6d 0000 0100 01 du.com..... 19:20:16.468176 IP (tos 0x0, ttl 128, id 182, offset 0, flags [none], proto: UDP (17), length: 118) 192.168.27.2.53 > 192.168.27.129.56183: [udp sum ok] 8002 q: A? www.baidu.com. 3/0/0 www.baidu.com. CNAME www.a.shifen.com., www.a.shifen.com. A 61.135.169.105, www.a.shifen.com. A 61.135.169.125 (90) 0x0000: 4500 0076 00b6 0000 8011 81ed c0a8 1b02 E..v............ 0x0010: c0a8 1b81 0035 db77 0062 48e9 1f42 8180 .....5.w.bH..B.. 0x0020: 0001 0003 0000 0000 0377 7777 0562 6169 .........www.bai 0x0030: 6475 0363 6f6d 0000 0100 01c0 0c00 0500 du.com.......... 0x0040: 0100 0000 0500 0f03 7777 7701 6106 7368 ........www.a.sh 0x0050: 6966 656e c016 c02b 0001 0001 0000 0005 ifen...+........ 0x0060: 0004 3d87 a969 c02b 0001 0001 0000 0005 ..=..i.+........ 0x0070: 0004 3d87 a97d ..=..} 2 packets captured 3 packets received by filter 0 packets dropped by kernel
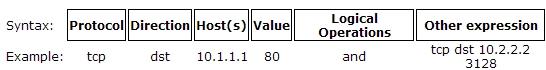
Common Syntax
Expressions allow you to trim out various types of traffic and find exactly what you're looking for. Mastering the expressions and learning to combine them creatively is what makes one truly powerful with tcpdump.
expression
select which packets will be dumped. If no expression is given, all packets on the net will be dumped. Otherwise, only packets for which expression is 'True' will be dumped.
There are three different kinds of qualifier.
type qualifiers say what kind of thing the id name or number refers to. Possible types are host, net and port. If there is no type qualifier, host is assumed.
dir qualifiers specify a particular transfer direction to and/or from id. Possible directions are src, dst, src or dst and src and dst. If there is no dir qualifier, src or dst is assumed.
proto qualifiers restrict the match to a particular protocol. Possible protos are: ether, fddi, tr, ip, ip6, arp, rarp, decnet, tcp and udp. E.g 'tcp src 192.168.1.2' . If there is no proto qualifier, all protocols consistent with the type are assumed.
Expressions are nice, but the real magic of tcpdump comes from the ability to combine them in creative ways in order to isolate exactly what you're looking for. There are three ways to do combinations, and if you've studied computers at all they'll be pretty familar to you:

舉例說明:
### type ## host # tcpdump host 1.2.3.4 ## net # tcpdump net 1.2.3.0/24 # tcpdump net 1.2 ## port # tcpdump port 80 ## src, dst # tcpdump src 1.2.3.4 # tcpdump dst 1.2.3.4 ## proto # tcpdump icmp ### type, dir, proto # tcpdump 'src port 3306 and tcp' # tcpdump 'udp and src port 53'
Writing to a File
tcpdump allows you to send what you're capturing to a file for later use using the -w option, and then to read it back using the -r option. This is an excellent way to capture raw traffic and then run it through various tools later.
The traffic captured in this way is stored in tcpdump format, which is pretty much universal in the network analysis space. This means it can be read in by all sorts of tools, including Wireshark, Snort, etc.
## capture all port 80 traffic to a file # tcpdump -s 1514 port 80 -w capture_file ## read captured traffic back into tcpdump # tcpdump -r capture_file
More Examples
# tcpdump -nnvvS 'src 10.5.2.3 and dst port 3306' # tcpdump 'src 10.0.2.4 and (dst port 3306 or 22)' ## 你懂的 # [root@localhost ~]# tcpdump -i eth0 -nnvvXS -s1514 'port 22 or port 23 or port 25 or port 110' | egrep -i 'pass=|pwd=|log=|login=|user=|username=|pw=|passw=|passwd=|pass:|user:|username:|password:|login:|pass |user ' -B20
http://danielmiessler.com/study/tcpdump/
http://openmaniak.com/tcpdump.php
http://www.binarytides.com/tcpdump-tutorial-sniffing-analysing-packets/
http://www.cnblogs.com/ggjucheng/archive/2012/01/14/2322659.html (good)
http://blog.csdn.net/langeldep/article/details/6156818
http://roclinux.cn/?p=2474
http://www.chinaunix.net/old_jh/29/674578.html
http://blog.chinaunix.net/uid-10328574-id-2951040.html
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。