您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
假定我們在Kubernetes 指定兩個worker節點中部署了ingress nginx來為后端的pod做proxy,這時候我們就需要通過keepalived實現高可用,提供對外的VIP
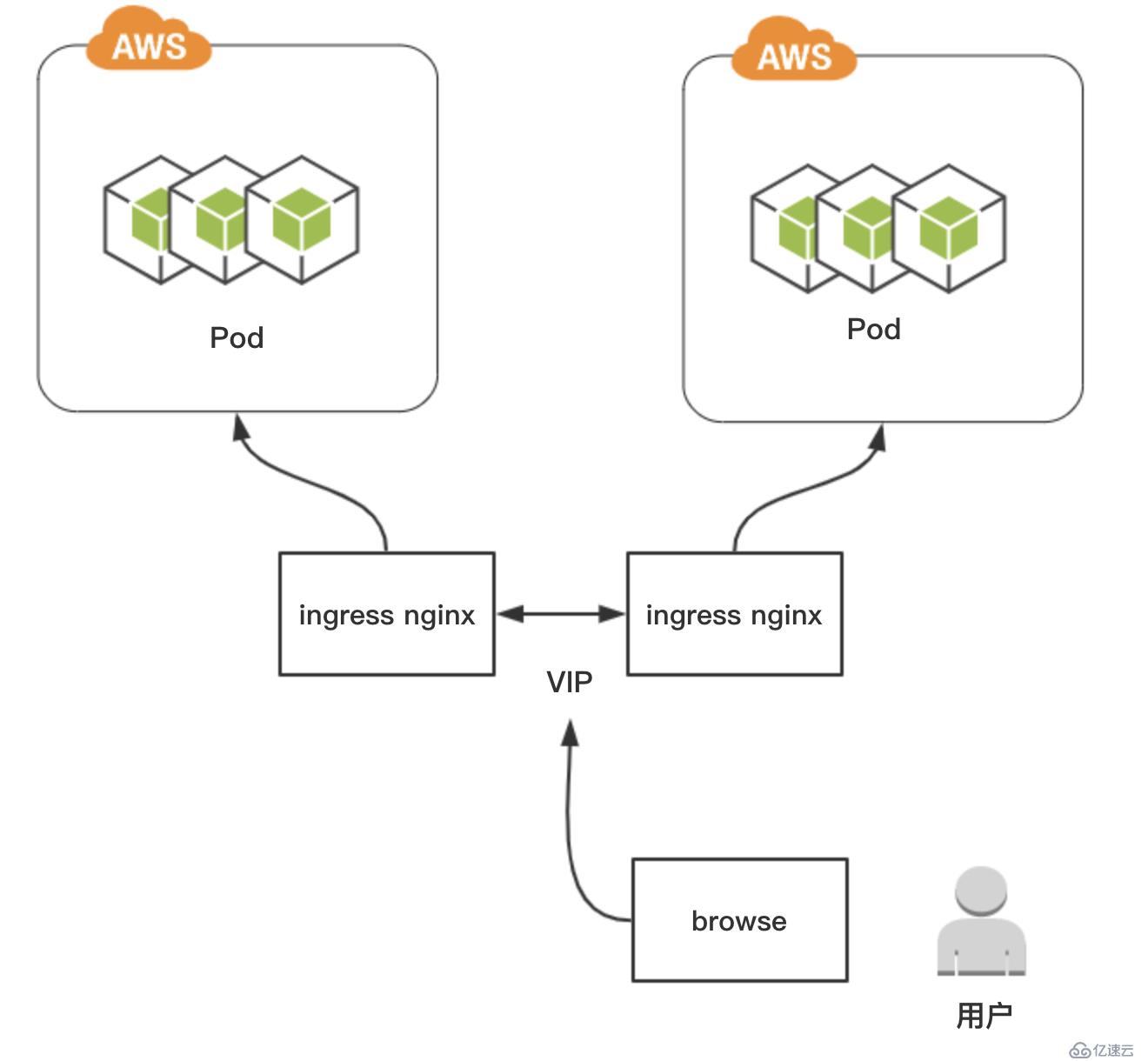
首先我們要先確保有兩個worker節點部署了ingress nginx
在本實驗中,環境如下:
| IP地址 | 主機名 | 描述 |
|---|---|---|
| 10.0.0.31 | k8s-master01 | |
| 10.0.0.34 | k8s-node02 | ingress nginx、keepalived |
| 10.0.0.35 | k8s-node03 | ingress nginx、keepalived |
1、查看ingress nginx狀態
[root@k8s-master01 Ingress]# kubectl get pod -n ingress-nginx -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ingress-controller-85bd8789cd-8c4xh 1/1 Running 0 62s 10.0.0.34 k8s-node02 <none> <none>
nginx-ingress-controller-85bd8789cd-mhd8n 0/1 Pending 0 3s <none> <none> <none> <none>
nginx-ingress-controller-85ff8dfd88-vqkhx 1/1 Running 0 3m56s 10.0.0.35 k8s-node03 <none> <none>創建一個用于測試環境的namespace
kubectl create namespace test2、部署一個Deployment(用于測試)
apiVersion: apps/v1
kind: Deployment
metadata:
name: myweb-deploy
# 部署在測試環境
namespace: test
spec:
replicas: 3
selector:
matchLabels:
name: myweb
type: test
template:
metadata:
labels:
name: myweb
type: test
spec:
containers:
- name: nginx
image: nginx:1.13
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
---
# service
apiVersion: v1
kind: Service
metadata:
name: myweb-svc
spec:
selector:
name: myweb
type: test
ports:
- port: 80
targetPort: 80
protocol: TCP
---
# ingress
執行kubectl create 創建deployment
kubectl create -f myweb-demo.yaml查看deployment是否部署成功
[root@k8s-master01 Project]# kubectl get pods -n test -o wide | grep "myweb"
myweb-deploy-6d586d7db4-2g5ll 1/1 Running 0 23s 10.244.3.240 k8s-node02 <none> <none>
myweb-deploy-6d586d7db4-cf7w7 1/1 Running 0 4m2s 10.244.1.132 k8s-node01 <none> <none>
myweb-deploy-6d586d7db4-rp5zc 1/1 Running 0 3m59s 10.244.2.5 k8s-node03 <none> <none>3、在兩個worker節點部署keepalived
VIP:10.0.0.130,接口:eth0
1.安裝keepalived
yum -y install keepalived1.k8s-node03節點作為master配置keepalived
[root@k8s-node03 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email_from Alexandre.Cassen@firewall.loc
router_id k8s-node03
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 110
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.130/24 dev eth0 label eth0:1
}
}2.k8s-node03節點作為配置keepalived
[root@k8s-node03 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id k8s-node03
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 110
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.130/24 dev eth0 label eth0:1
}
}3.k8s-node02節點配置keeplived
[root@k8s-node02 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id k8s-node02
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.130/24 dev eth0 label eth0:1
}
}4.兩個節點啟動keepalived并加入開機啟動
systemctl start keepalived.service
systemctl enable keepalived.service 啟動完成后檢查k8s-node03的IP地址是否已有VIP
[root@k8s-node03 ~]# ip add | grep "130"
inet 10.0.0.130/24 scope global secondary eth0:15.在宿主機上配置hosts文件,實現IP和域名的解析
10.0.0.130 myweb.app.com6.瀏覽器測試訪問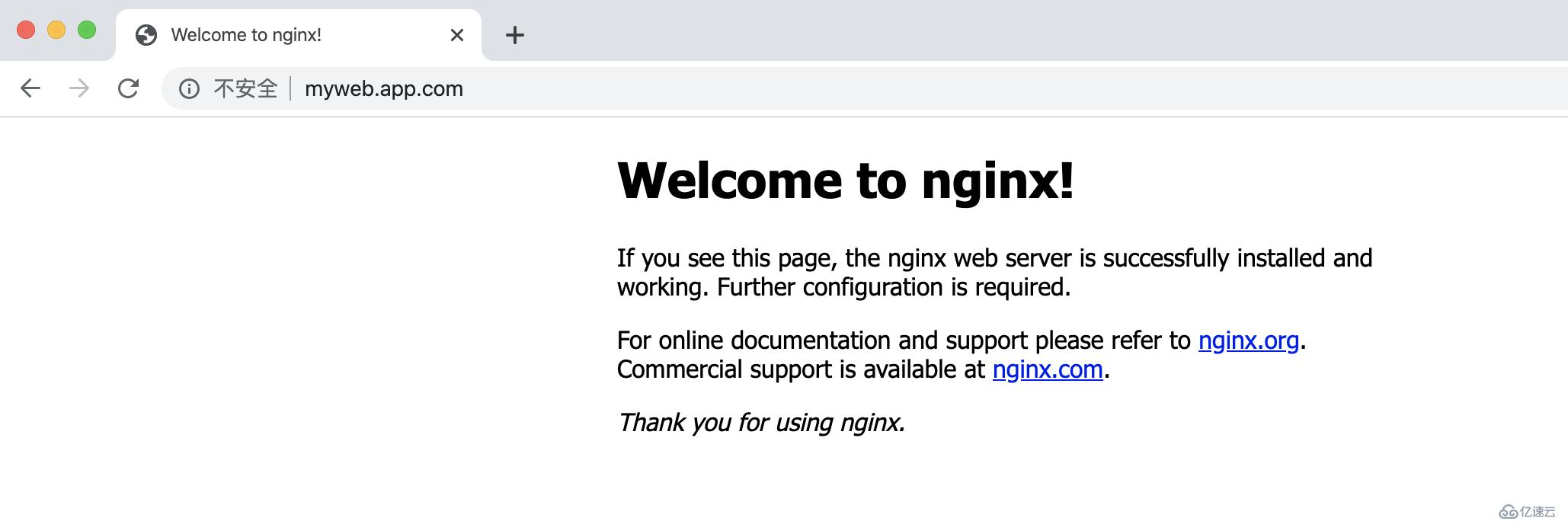
4.測試vip漂移
現在我將k8s-node03的keepalived進程關閉,那么vip就會漂移到k8s-node02
[root@k8s-node03 ~]# systemctl stop keepalived.service
// 在k8s-node02上查看VIP
[root@k8s-node02 ~]# ip add | grep "130"
inet 10.0.0.130/24 scope global secondary eth0:1再次訪問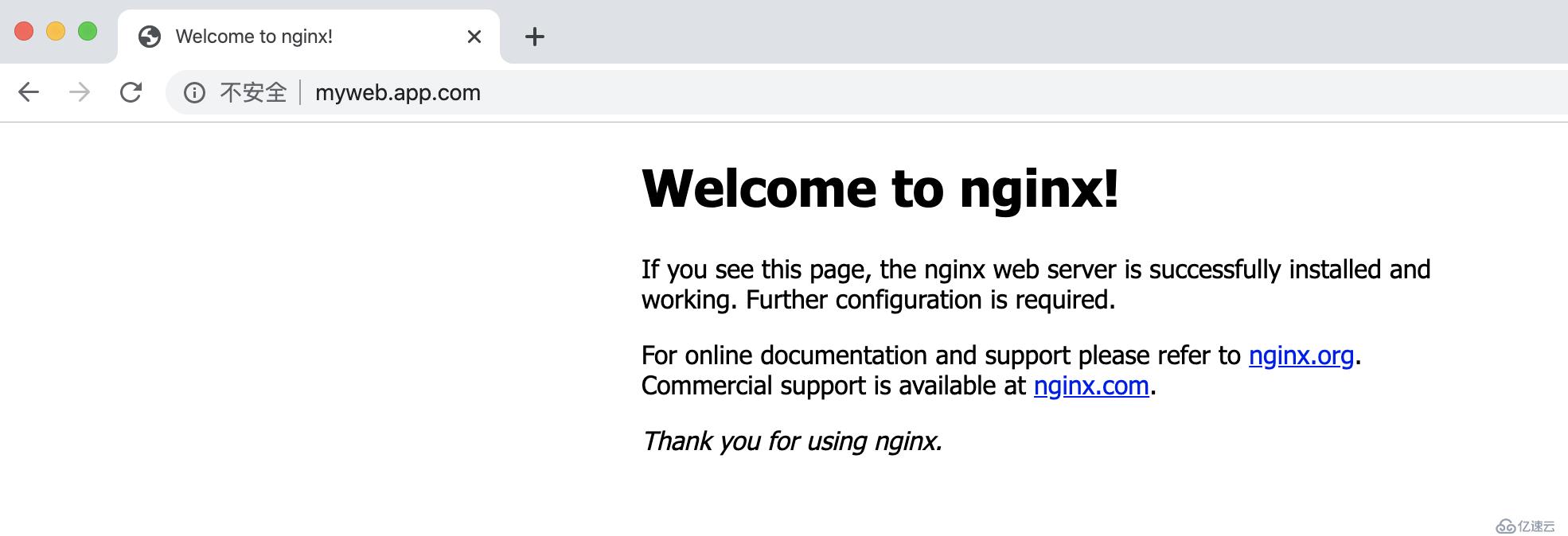
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。